Audit Logs
Successful operations and governance strategies rely partially on being able to audit actions taken in the service. Adhering to zero trust principles means that all activities performed in the tenant are available for review.
Microsoft 365 allows administrators to review activities that are performed either by users or administrators through the audit logs. Audit logs are available in the Microsoft Purview compliance portal (formerly known as the Microsoft 365 compliance center) and are located at https://compliance.microsoft.com/auditlogsearch.
Some audited actions include the following:
- File and page operations
- Sharing and access request activities
- Exchange mailbox activity
- User administration activity
- Role administration activity
- eDiscovery tasks
- Microsoft Teams operations
- Exchange admin operations
Previously, audit logging was disabled by default. In new organizations, Microsoft has automatically enabled it; however, it can still be disabled manually via an administrator.
Audited activities
For a complete list of all currently audited activities, please check out the following documentation: https://docs.microsoft.com/en-us/office365/ securitycompliance/search-the-audit-log-in-security-and-compliance.
In your position as administrator, you should check and ensure that auditing is turned on. Administrators can enable this by opening the Microsoft Purview compliance portal and clicking on Start recording user and admin activity, as shown in Figure 7.4:
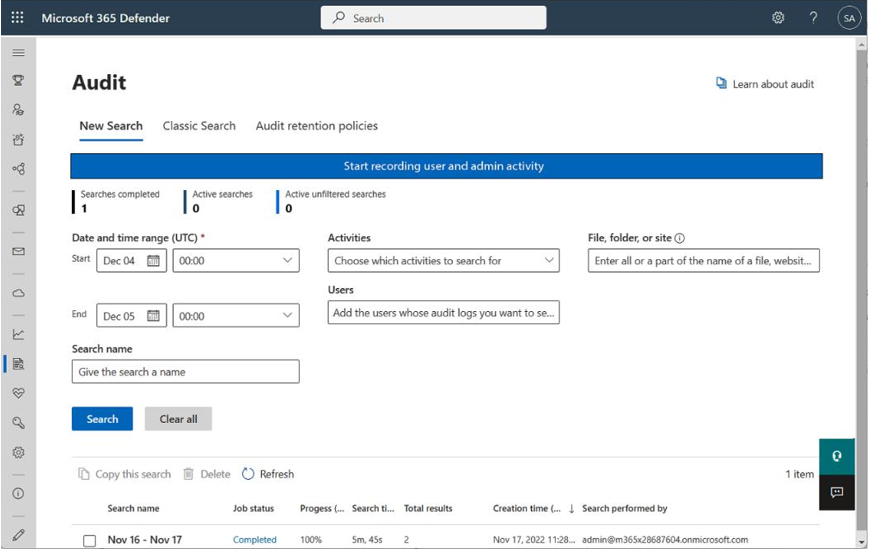
Figure 7.4 – Enabling auditing
When viewing audit logs, administrators can filter them according to the following options:
- Activities
- Start date
- End date
- Users
- File, folder, or site
Currently, Microsoft 365 audit logs are retained in the service for 90 days for users with aMicrosoft 365 Enterprise E3 license, or one year for users with a Microsoft 365 EnterpriseE5 license. If anorganization wants to retain data for a longer period, it will need to plan and deploy a solution to capture that data, such as Azure Sentinel, Log Analytics, or an on-premises Security Information and Event Management (SIEM) product. This can be accomplished through PowerShell or with the Office 365 Management Activity API.
To export a list of audit log entries, an administrator can open the audited data and select individual entries to view and export. You can also download all of the entries by clicking Export and then selecting Download all results, as shown in Figure 7.5:
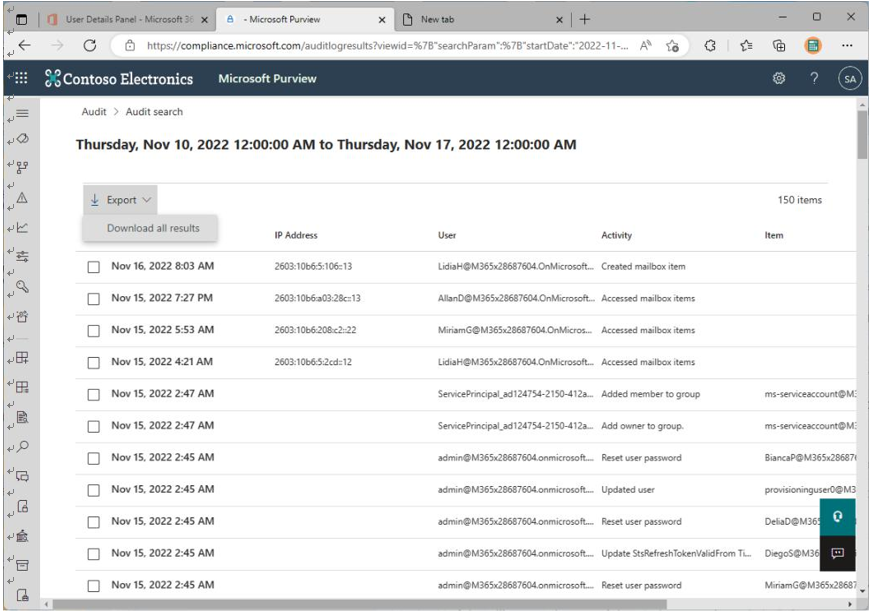
Figure 7.5 – Exporting audit search results to a CSV file
- report will be made available to the administrator in Comma-Separated Values (CSV) format. Next, you will review the features of audit retention policies.