Audit Retention Policies
As mentioned in the previous section, audit logs have a default retention period: users with E3 licenses are enabled for 90-day retention, and users with E5 licenses are enabled for up to a year’s retention.
With the Microsoft Purview compliance center, you can create retention policies to govern how long the audit data will be preserved. In addition to the default policy terms, you can purchase and apply Microsoft 365 Advanced Compliance licenses for 10 years of additional audit log retention. Audit retention policies are scoped to users and record types, as shown in Figure 7.6:
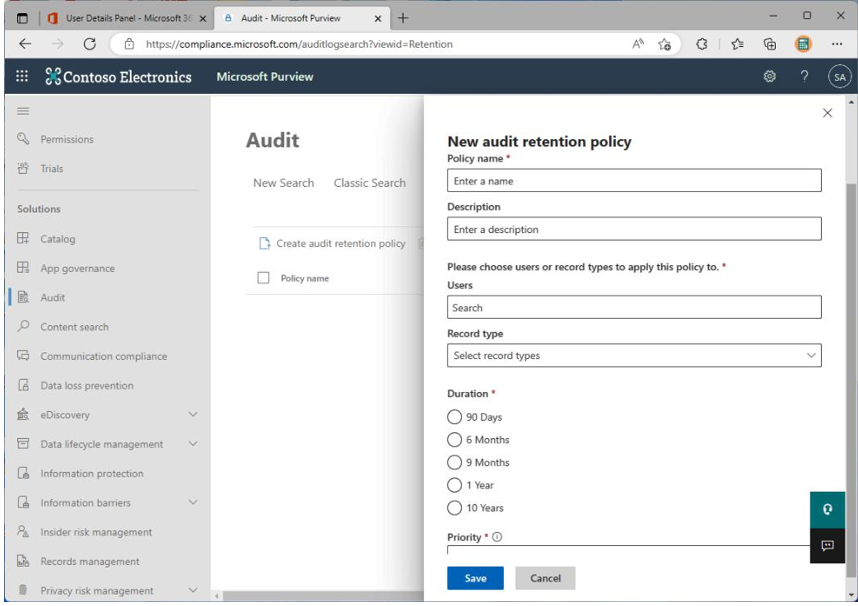
Figure 7.6 – Audit retention policy
A tenant can have up to 50 audit retention policies.
Alerts
As an administrator, a common scenario for you is to alert an operations team whenever a specific activity occurs. The following are examples:
- Notifying a user who shared a document externally
- Blocking unauthorized administrators
- Blocking a potentially compromised account that is performing a suspicious activity
To do that, you can leverage activity alerts, which allow you to create rules based on conditions. Sample conditions might be files being shared externally, a DLP policy match, modifying the permissions of a SharePoint site, and so on.
Whenever a user does anything that meets an alert’s conditions, an email will be sent to the recipient configured in the alert, notifying them about the flagged activity. Figure 7.7 shows an example of a notification email:
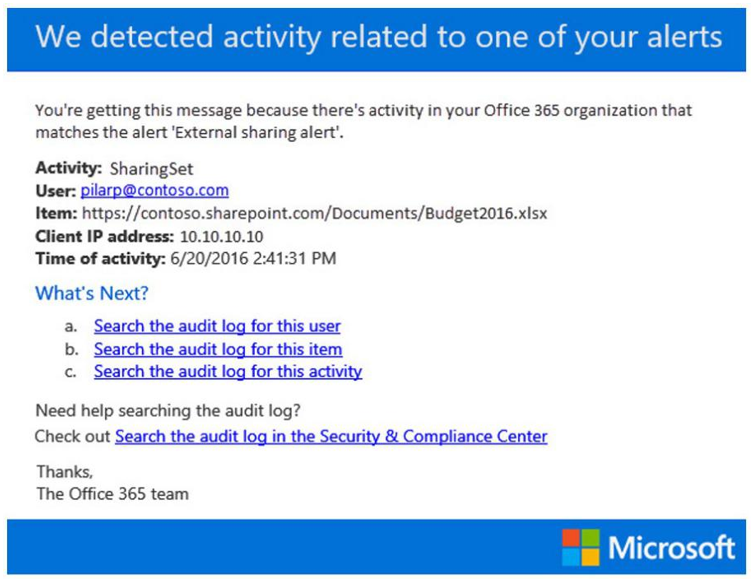
Figure 7.7 – An activity alert email triggered from a user-specific action
From here, you can open the audit log search in the Microsoft Purview compliance center to review and investigate the user activities. Administrators can automate activities that will be executed whenever a set of actions occur. To accomplish this, they can leverage Microsoft Defender for Cloud Apps (MDA), formerly known as Microsoft Cloud App Security. MDA allows administrators to create policies to perform the following actions:
- Suspend a user
- Require a user to sign in again
- Notify a user
Note
MDA policies, including activity, file, and anomaly detection, are out of the scope of this exam. You can learn more about MDA here: https://learn.microsoft.com/en-us/ defender-cloud-apps/what-is-defender-for-cloud-apps.
For example, say a user triggers a specific activity alert that warrants that the user be suspended. Instead of you (the administrator) being notified of an anomaly via email, launching a portal, navigating to the alert logs, and then performing the suspension manually, MDA can execute a workflow to automatically take the required action.
Alerts that were triggered are reviewed in the MDA portal (https://portal.cloudappsecurity.
com) so that you, as an administrator, can act where appropriate (see Figure 7.8):
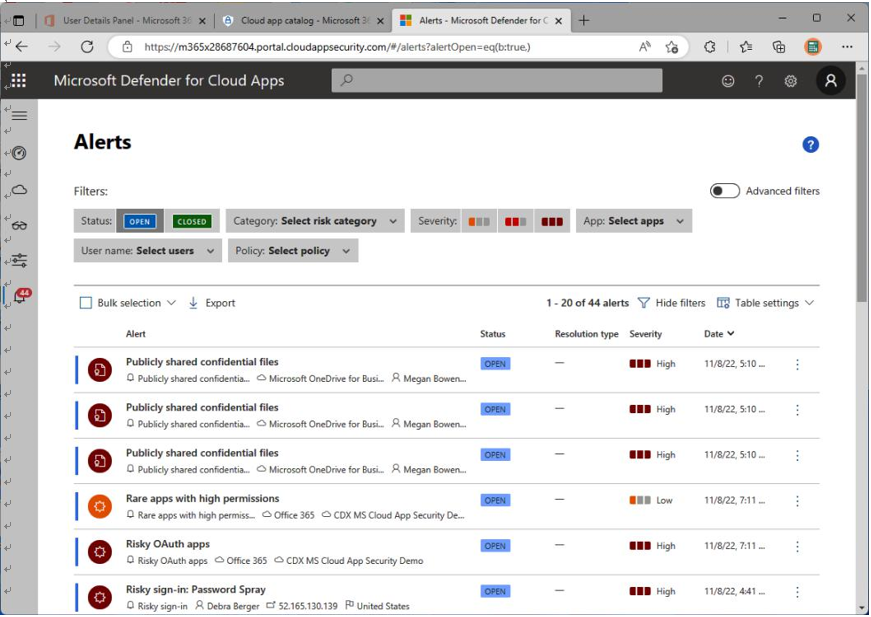
Figure 7.8 – MDA alerts
There are multiple ways to filter the results, such as by resolution status, category, and severity.
Administrators can also export the results to a CSV.