Auditing
Auditing determines which actions were executed by which identity, and the time those actions were performed. As described earlier, Microsoft 365 allows administrators to audit actions that are performed in the service regarding file sharing and collaboration, syncing, deletion, and access. A comprehensive zero-trust policy will ensure that auditing data is captured for security analysis purposes.
The main auditing activities for files are as follows:
- Accessed file
- Copied file
- Deleted file
- Deleted file from the recycle bin
- Deleted file from the second stage recycle bin
- Downloaded file
- Moved file
- Uploaded file
In addition, sharing is also part of the audited log activities. The main sharing audited activities are listed as follows:
- Created access request
- Created a company-shareable link
- Created a sharing invitation
- Shared a file, folder, or site
- Used a company-shareable link
- Withdrew sharing invitation
A view of the audited sharing activities on the Audit screen inside the Microsoft Purview compliance center located at https://compliance.microsoft.com/auditlogsearch can be seen in Figure 7.16:
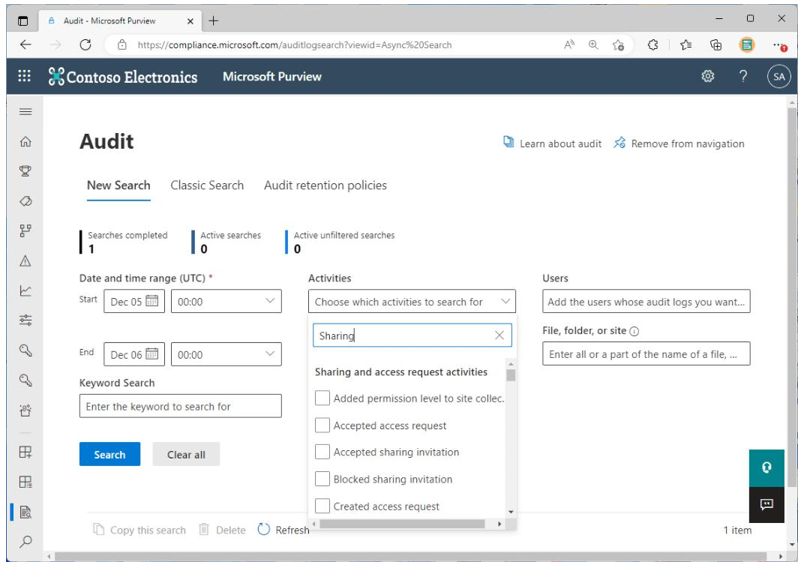
Figure 7.16 – Audit activities
As mentioned earlier, administrators should leverage audit logs, along with activity alerts and Cloud App Security (CAS) policies, to learn which actions are being taken by users and administratorsregarding files and sharing inside their organization.
Classification and Protection
Microsoft 365 allows users and administrators to classify and protect documents (stored in OneDrive, SharePoint, or locally) as well as email messages, using the Azure Information Protection (AIP) service. AIP is part of Microsoft Purview Information Protection (formerlyMicrosoft Information Protection (MIP)).
From a zero-trust perspective, classification is important because it can be used to influence policy (both organizational policy and technology policy) to restrict access to data based on business needs.
Administrators can create classification labels and configure the actions available to users of the label. For example, a label can be configured to allow or deny the ability to take screenshots, copy content, or print it. Labels can be used to prevent users from modifying the recipients of a message or forwarding it to others. Once the labels have been configured and published, users can apply them to protect documents, files, and emails.
Administrators can also audit and control how classification and encryption technologies are used across the organization. Content is classified using the following methods:
- Outlook
- Office applications such as Word or Excel
• EXO transport rules, which modify specific message properties throughout its transport
- Security and compliance center DLP rules
- Windows Explorer using the AIP unified labeling client
After classification has been applied, the email message or document will display its tag, and users—if authorized to open the file—will be able to review which actions they are allowed to take on that information (Figure 7.17):
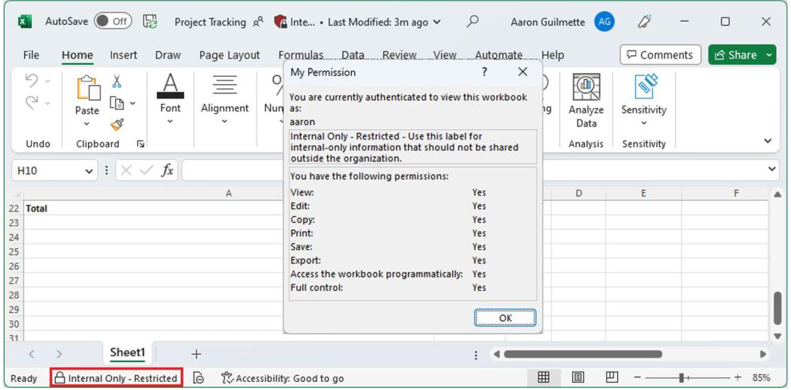
Figure 7.17 – Classification label
AIP is part of both Microsoft 365 E3 and Microsoft 365 E5. In Microsoft 365 E3, users must perform data classification manually. With Microsoft 365 E5, administrators can configure classification so that it happens automatically, such as when an application detects sensitive content such as credit cards or social security numbers.