Describe Identity Concepts
When describing how users access Microsoft 365 services, the identity and authentication processes are the key concepts to understand. In this section, you will learn three core identity models (as well as some sub-features of each) and how they work in the context of Microsoft 365. The three models are as follows:
- On-premises identity
- Cloud identity
- Hybrid or synchronized identity
You will now look at each in detail.
Directory Services
Directory services is a broad term that can be used to describe the identity storage and authentication system in an organized computer environment. It stores information regarding objects and resources and enables other users, devices, and services in a type of custom database called a directory. It also enables other users, devices, and services to access this information.
A directory may have policy and configuration information stored in it. This policy and configuration information is used to manage the operation of the directory service.
A directory service may also provide an authentication and authorization engine to act as a gatekeeper of access to information.
On-Premises Identity
Active Directory Domain Services (ADDS, commonly referred to as just AD) is an on-premises
directory service solution that is a part of the Windows Server operating system. AD is organized in
- hierarchical structure comprising forests, trees, domains, organizational units, and leaf objects (such as users, contacts, computers, and groups). Everything in a forest shares a single schema—a type of configuration definition used to describe the available object types, parameters, properties, and attributes that objects can have.
In Figure 8.1, the ContosoEnterprises.com circle represents the top-most container object—a forest. A forest can have one or more trees (the shaded boxes), and inside each of those trees can be
one or more domains (such as fabrikam.com or contoso.com). These domains can be nested inside of each other, each representing its own security boundary.
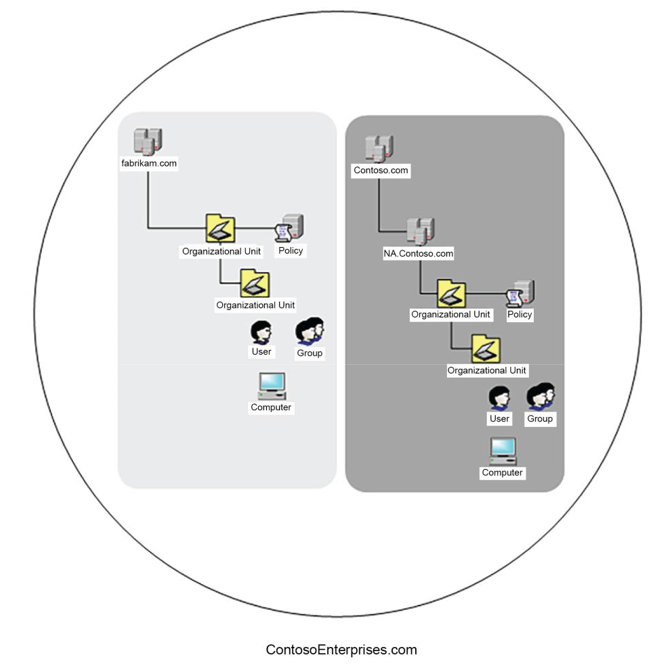
Figure 8.1 – Active Directory diagram
Each domain has its own internal hierarchal structure comprised of organizational units. Organizational units can contain objects such as users, groups, contacts, computers, and printers.
In addition, configuration items such as Group Policy Objects can be stored or linked at any level of the hierarchy. Group Policy Objects can be used to specify particular configuration settings that apply to security principals (such as users or computers).
With Active Directory, delegated security controls (the ability to manage objects) and policies can be inherited from a parent object to a child object. An administrator can be delegated control at any level of the directory (from the domain level to any depth of organizational unit). They can manage all objects from that management delegation point onward. Likewise, policies can be created and linked (applied) at any level of the directory and will flow downward to child containers.
Forests and domains can establish security relationships called trusts with each other. Trusts allow objects in one forest or domain to access resources in another forest or domain and can be one-way or two-way (bi-directional).
Next, you’ll explore the modern cloud identity concepts.