Device Management
Microsoft 365 allows administrators to manage devices that are used to connect to services. Administrators can enforce features and stipulations, such as requiring a password to unlock a device, ensuring that the device is not rooted or jailbroken, and selectively wiping company data from the device. The following two services are used to manage devices:
- Intune: Intune offers the ability to manage device certificates, Wi-Fi, Virtual Private Networks (VPNs), and email profiles, deploy apps to users, manage app protection as well as device compliance, prevent jailbroken/rooted devices from accessing corporate resources, define password policies, and disable cameras. Intune is managed through the Microsoft Endpoint Manager (MEM) admin center (https://endpoint.microsoft.com).
- Mobile Device Management (MDM) for Office 365: MDM for Office 365 provides a subset of Intune features, such as preventing the connection of jailbroken or rooted devices, disabling cameras, and defining a password policy.
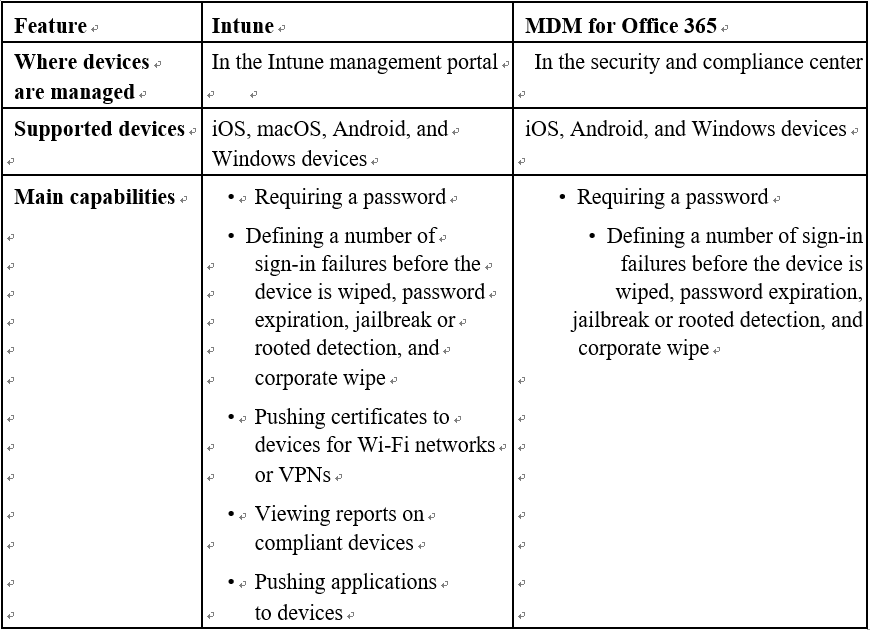
Table 7.1 lists the main differences between MDM for Office and Intune capabilities:
In addition to MDM scenarios, Intune provides Mobile Application Management (MAM) capabilities, allowing controls to be applied to specific applications, such as the following:
- Requiring a Personal Identification Number (PIN) to open the app
- Encrypting corporate app data
- Data wipe (full device or selective data wipe)
- Blocking copy and paste between corporate and personal applications
Organizations that already have an MDM solution to manage corporate devices can still use Intune to manage applications with MAM.
Note
You can find more information on MAM at https://docs.microsoft.com/en-us/ intune/apps/app-protection-policy.