Role Management
Permissions allow organizations to provide certain individuals with elevated access so that they can perform specific operations in the service. A common strategy that is shared across different Microsoft 365 admin centers is Role-Based Access Control (RBAC). RBAC will allow—under the minimum level of permissions needed—users (categorized by roles) to execute their tasks and only their tasks. Utilizing roles is a key way to employ a least-privilege access model.
Microsoft 365 has a granular permissions model that allows organizations to have multiple administrators whose administrative abilities are scoped to certain groups of tasks. Some of the roles that are available in Microsoft 365 are outlined here:
- Billing admin: This role makes purchases, manages subscriptions and service requests, and monitors the health service.
- Global admin: This role is the most permissive role with the rights to access and modify all configurations in all the admin centers. It can also reset the passwords of all users and add and manage domains.
- Exchange admin: With full access to the Exchange Online (EXO) admin center, this role manages Microsoft 365 groups and service requests, and monitors service health.
- Group admin: The role creates and manages groups, including group naming and expiration policies.
- Helpdesk admin: This role can reset passwords for non-admin users, help users sign out, manage service requests, and monitor service health. The helpdesk admin can force users to sign out. Users with this role can only reset passwords for users that do not have other directory roles (except the Directory reader, Guest inviter, Helpdesk admin, Message center reader, and Reports reader roles).
- License admin: This role can assign and remove user licenses and usage locations.
- Message center privacy reader: This role grants permission to view the message center posts (including posts about data privacy), as well as view domains, groups, and subscriptions.
- Office Apps admin: Users with this role can use the Cloud Policy service to create and manage cloud-based policies for Microsoft 365 apps, create and manage service requests, monitor service health information, and manage the What’s New content for Microsoft 365 apps.
- Password admin: This role resets passwords for all non-administrative users.
- Power Platform admin: The Power Platform admin can manage the admin features for Power Apps and Data Loss Prevention (DLP). This role can also create and manage service requests as well as monitor service health information.
- Reports reader: The reader accesses the reports dashboard, Power BI adoption content packs,sign-in reports, and the Microsoft Graph reportingApplication Programming Interface (API).
- Global reader: Users in this role can read settings and administrative information across Microsoft 365 services but cannot take management actions. Global reader is the read-only counterpart to Global admin.
- Service Support admin: The Service Support admin can open and manage service requests, view message center posts, and monitor service health messages.
- SharePoint admin: This role has full access to theSharePoint Online (SPO) admin center, manages Microsoft 365 groups and service requests, and monitors service health.
- Teams administrator: This role has full access to the Teams admin center, manages Microsoft 365 groups and service requests, and monitors service health.
- Teams communications administrator: This role assigns telephone numbers, creates and manages voice and meeting policies, and reads call analytics.
- Teams device administrator: This role configures and manages devices used for Microsoft Teams services, such as Teams Rooms, Teams displays, and phones.
- User admin: This role resets user passwords, manages users and groups, manages service requests, and monitors service health.
Note
While it’s not important to know all of the roles for the MS-900 exam, it’s important to be familiar with a few core roles (such as Global admin, Billing admin, User admin, Helpdesk admin, Password admin, and License admin) and the overall concepts of role-based administration. You can find a more complete list at https://learn.microsoft.com/en-us/azure/ active-directory/roles/permissions-reference.
To assign a role to a user in the Microsoft 365 admin center, an administrator with proper permissions can edit a user’s properties and assign an administrator role under Manage admin roles, as shown in Figure 7.1:
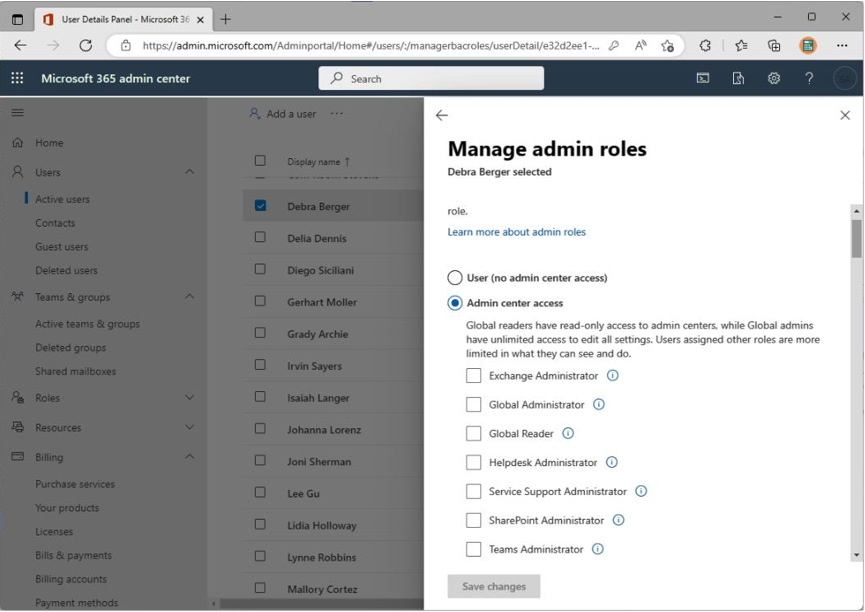
Figure 7.1 – Assigning an admin role
Additionally, more granular roles can be assigned in the Azure Active Directory (AAD) Roles and administrators blade, which is available in the Azure portal (https://aad.portal.azure. com), as shown in Figure 7.2:
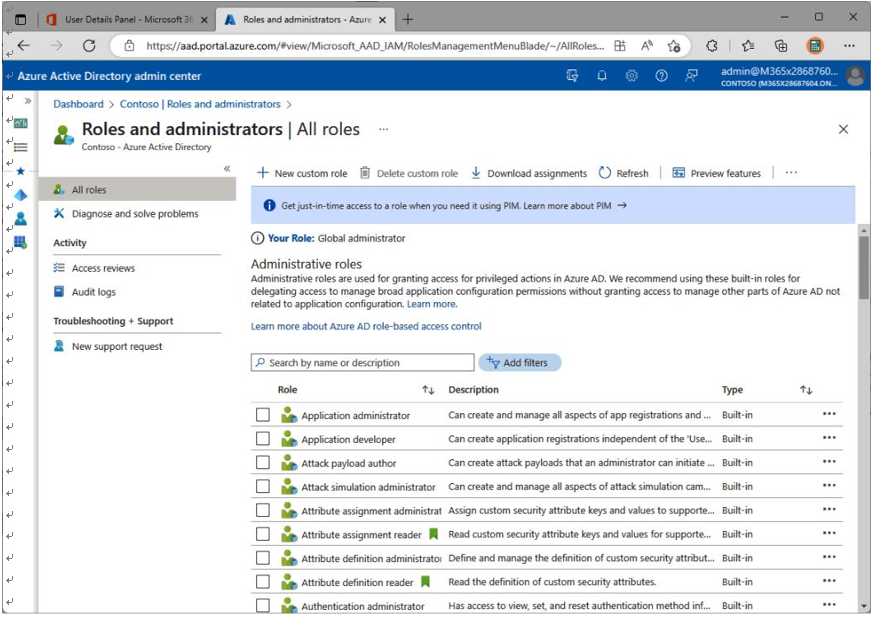
Figure 7.2 – AAD Roles and administrators blade
As part of a least-privilege access model, organizations can also use Privileged Identity Management (PIM). PIM allows designated users to be granted elevated permissions for a period of time and is configured with a series of workflows to ensure proper approval is granted before assigning the role permissions. With this feature, organizations can significantly limit the number of fully privileged accounts in their environment, reducing their attack surface.
AAD PIM is configured through the Azure portal (navigate to https://portal.azure.com and search for Privileged Identity), as shown in Figure 7.3:
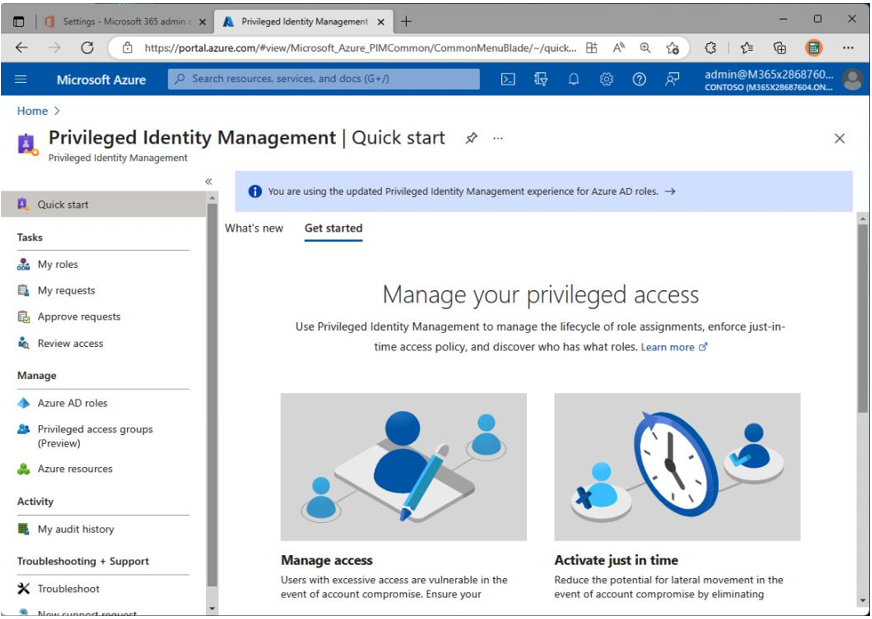
Figure 7.3 – Privileged Identity Management
Organizations should follow best practices when considering their permission, role, and administration strategies. Some recommendations include the following:
- Have no more than four and no less than two global admins.
- Whenever possible, assign the least permissive role to administrators.
- Require Multi-Factor Authentication (MFA) from all admins and end users.
You will read more about recommendations later in this chapter.